Keep your guard up
Vehicle-to-vehicle (V2V) and vehicle-to-infrastructure (V2I) communications are emerging for next-generation vehicles in surface transportation systems.
Using V2V and V2I communications, connected vehicles (CVs) share information with other vehicles and with transportation infrastructure, which increases traffic safety, provides efficient mobility services and reduces fuel consumption. To use the full potential of CV technology, these V2V and V2I communication-enabled vehicles can leverage the existing communication technology (such as dedicated short-range communications [DSRC] and 4G) and emerging communication technology (such as 5G). However, the risk of cyberattacks increases as vehicles become more connected through the Internet and wireless networks. One of the cyberattack gateways to connected vehicles is the V2I communication interface. Cyberattacks on V2I communications that are not properly secured can have devastating consequences. V2I communications present a variety of vulnerabilities, which create an attractive target for hackers. For example, hackers could take control of traffic signals, create crashes and even cause a breakdown of the roadway traffic system. Thus, it is critical to develop new and adaptive security solutions to protect people from this vulnerability.
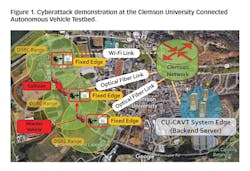
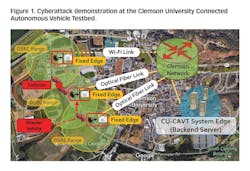
A CV environment consists of diverse data collection, communication and dissemination, and computing infrastructure systems, which are vulnerable to cyberattacks the same as all traditional computing environments. For example, the Clemson Connected Autonomous Vehicle Testbed (CU-CAVT) is comprised of a layered CV architecture, which contains roadside infrastructure or Fixed Edges, regional infrastructure or System Edges, and CVs or Mobile Edges (see Figure 1). Edges communicate with each other through a heterogeneous wireless network (HetNet) in CU-CAVT. As shown in Figure 1, if an attacker instigates a cyberattack on the Fixed Edges or roadside infrastructure, it may create a collision between vehicles. Hence, cyberattacks can jeopardize the expected safety benefits, as well as mobility, energy and environmental benefits expected from CV applications. Preventing cyberattacks that can lead to severe traffic incidents has become one of the primary concerns of CV applications. In our project, we have investigated the impact of cyberattacks on V2I communication from a CV application perspective. Then, we developed a novel V2I cybersecurity platform, CVGuard, which can detect and prevent cyberattacks on the V2I environment.
Our approach to CVGuard
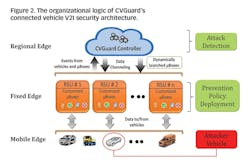
This software-based cybersecurity platform leverages three emerging technologies: Edge computing, Software-defined network (SDN) and Network Function Virtualization (NFV). The primary goal of the platform is to detect and isolate any cyberattacks in a V2I environment before they can negatively affect vehicles or transportation networks. Figure 2 shows a high-level architecture of CVGuard, which contains two major components: 1.) Customized microBoxes (portable network-security software module): These portable software modules are situated in each Fixed Edge (e.g., roadside units [RSUs]) that communicate with connected vehicles or any other infrastructure devices, and act as security gateways for each vehicle (Mobile Edge). They also provide dynamic attack capturing and analysis abilities for the V2I communication interfaces; 2.) Platform controller: a logically centralized Regional Edge which resides in the cloud where it monitors the context of different vehicles, RSUs and V2I communications. Since the controller is inside a cloud as a Regional Edge, it can virtualize entire classes of network nodes (e.g., routers, switches), network functions and services (e.g., intrusion detection and prevention systems, firewalls), and network address translation gateways.
The controller also identifies security threats, analyzes them, and controls microBoxes to eliminate the threats. RSUs become the entry point for potential V2I cyberattacks, and the microBoxes in each RSU perform computation functions on incoming data near the edge to detect cyberattacks in the CVGuard. To provide better service and manage available resources, security modules need to consume as few resources as possible such as memory and processing time. The software security modules or microBoxes ensure an efficient use of resources in an RSU. These microBoxes are only executed when needed and are erased when no longer necessary. Communication between RSUs also is necessary to disseminate the attack information among neighboring RSUs. This communication is facilitated by SDN to propagate the attack information and prevention policies to and from the controller and nearby RSUs. By leveraging NFV and SDN technologies, the controller can create or erase security modules or microBoxes. Furthermore, the controller acts as a centralized security controller to enable dynamic interoperation and automatic reconfiguration of software security modules, which are distributed between different RSUs.
In action
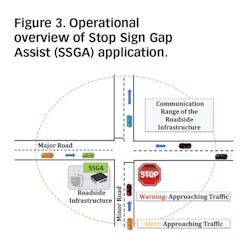
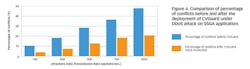
Key challenges such as scalability, resiliency and future usability were considered in designing the platform. In simulation, a case study using a distributed denial of service (DDoS) attack on the V2I “Stop Sign Gap Assist” (SSGA) application, shows that CVGuard was effective in mitigating the adverse safety effects created by a DDoS attack. The SSGA application helps drivers on a minor road at a stop-signed intersection by providing a warning of unsafe gaps on the major road (Figure 3). The SSGA application collects data from connected vehicles from both the major and minor roads, and computes the safe gap of the major road in order to issue appropriate warnings and alerts to minor road vehicles.
In this case study, because of the DDoS attack, conflicts between the minor and major road vehicles at an unsignalized intersection that could have led to potential crashes were observed. We found that utilizing the security platform during a DDoS attack resulted in a reduced number of conflicts between vehicles, when compared with the number of conflicts without the platform in action. Analysis revealed that the strategies adopted by the program were successful in reducing conflicts by 60% where a DDoS attack compromised the SSGA application at an unsignalized and stop-signed intersection (Figure 4).
Now and in the future
Because the CV environment is rapidly evolving, the need for cybersecurity protection is inevitable in the near future. Hardware-based security solutions (e.g., hardware security modules) are not feasible because of cost and maintenance issues. Software-based solutions are much cheaper and dynamically configurable. However, the challenge lies in selecting appropriate methods to protect CVs against cybersecurity threats.
Emerging technologies, such as edge computing, SDN and NFV, exhibit great innovative potential in effective cybersecurity solutions for the CV environment. Our analysis shows that because of the DDoS attack, the data receiving rate (DRR) by V2I applications dropped to 10% during a DDoS attack compared to DDR of 93% during the normal operation (i.e., without the DDoS attack).
The experiment described here is limited to DDoS attacks. However, it is possible to develop detection and prevention mechanisms in the platform to deal with other types of attacks as well. Security rules and policies can be used in different combinations corresponding to the detection and prevention of different cyberattacks. These combinations are defined by the controller and can be adjusted depending on the type of attack. We are currently working on developing more modules for the platform to make the system more robust, scalable, flexible and elastic. Because this is a software-based solution, it will be possible for other researchers and developers to develop different modules to contribute to the continuous development of the platform. The Center for Connected Multimodal Mobility (C2M2) headquartered at Clemson University is currently conducting a variety of cybersecurity research in the field for protecting the CV environment. More extensive experiments are planned in the near future in the CU-CAVT to evaluate the effectiveness and efficiency of the system under different cybersecurity threats in a V2V and V2I environment.
The Center for Connected Multimodal Mobility (C2M2) at Clemson University is currently conducting field research on cybersecurity for CVs.
Acknowledgments: This article is based upon research supported by the Southeastern Transportation Center under O/E Grant 2016-1017, and U.S. DOT Center for Connected Multimodal Mobility (C2M2, a Tier 1 University Transpiration Center) grant.
-------------------------
About the author:
Chowdhury is a Eugene Douglas Mays endowed professor of transportation in the Glenn Department of Civil Engineering, Clemson University. Islam is a Ph.D. candidate in the Glenn Department of Civil Engineering, Clemson University. Li is a Ph.D. candidate in the division of computer science at the School of Computing, Clemson University. Hu is an assistant professor in the School of Computing, Clemson University.